SAML configuration with Azure AD
Note
SAML (Security Assertion Markup Language) is a single sign-on method that allows users to log in once and then gain access to other applications.
SAML authentication involves two parts:
- Service Provider: The application that the user is trying to connect to. In our case, this is S-Filer Portal.
- Identity Provider: Performs authentication and passes the user's identity to the service provider. In our case, this is Microsoft Azure AD.
SAML flow
- The unauthenticated user attempts to access the service provider.
- The service provider determines the identity providers available for authentication.
- The user enters their credentials to the selected identity provider with a SAML request.
- The identity provider validates the credentials and the assertion is sent back to the service provider.
- The user is now authorized to access the application.
Set up in the Azure portal
Implementing SAML requires steps that take place in the Azure portal and steps that take place in the S-Filer Portal administrative console.
The following steps are performed in the Azure portal and require having the necessary permissions to add a new Enterprise Application.
Step 1 - Connect to the Azure portal
Log in to the Azure portal (https://portal.azure.com/) using your browser and your login credentials.
Step 2 - Create a new "Enterprise Application"
Use the search bar present in the Azure Portal home page to find the Enterprise Application service. Once in the Enterprise Application screen, use the New application button in the top bar to create a new application:

Step 3 - Create your own application
When the new page is presented, click the Create Your Own Application button, then enter a name that identifies the S-Filer Portal application. Click Create.

Step 4 - Find the S-Filer Portal application
Type in the service search box: App registrations

Type in the application search box: SFILER-App (use the name you chose when creating the application) and select the newly created application from the list.

Step 5 - Authentication configuration
Click on Authentication, then Add a platform and finally Web.

Step 6 - Specify the redirection URI
Enter the domain name of S-Filer Portal followed by /sfiler/LoginSamlAzureCallback.action as the "redirect URI" (e.g. https://[YOUR.SFILER-DOMAIN.COM]/sfiler/LoginSamlAzureCallback.action. Make a note of this value somewhere and click on Configure. This URL comes from the environment on which S-Filer Portal is running. It should be a URL that is accessible to users who want to use the Azure SAML functionality.

Step 7 - Configure API exposure
Click on the Expose an API tab, then on Set Application ID URI.

Enter an ID for the application. Write this value down somewhere. Then click on Save.

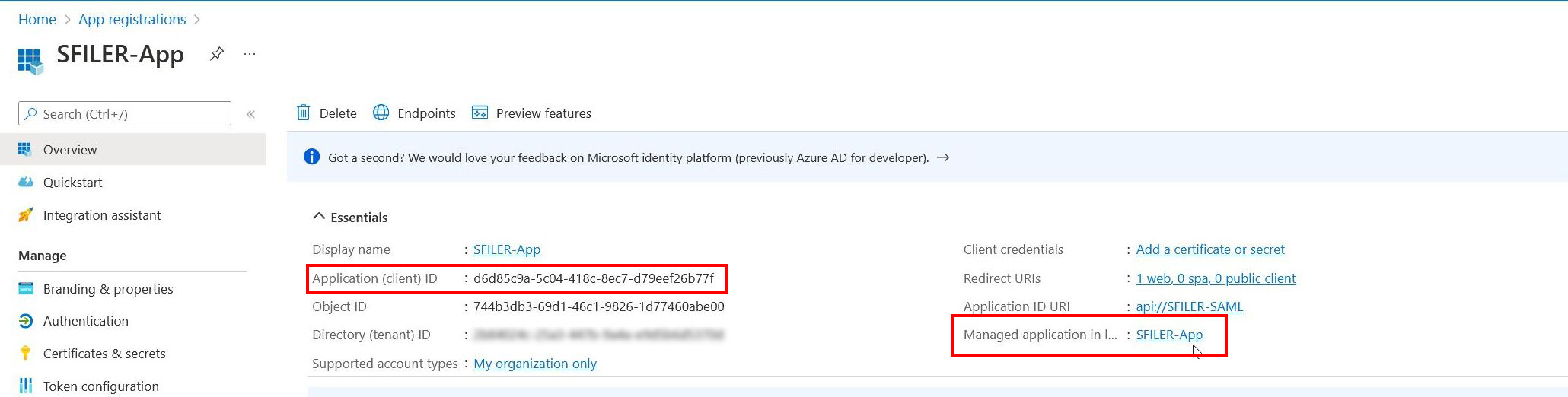
Click on the Overview tab, then on Managed application in ...
Note
You'll need the 'Application (client) ID' values for step 2 of the 'Configuration in S-Filer Portal' section.
Click on Single sign-on, then SAML.

In the Basic SAML Configuration box, click on Edit.

In the ID field, enter the value that was set for the application ID. Click on the Default checkbox. In the Reply URL field enter the value that was set for Redirect URIs. Click on the Default check box.
Click on Save.

The save should be confirmed in the detail page.

Copy and keep the value of Application federation metadata URL in the SAML signature certificate box.

Click on the Users and groups tab, then on Add a user/group. It is in this screen that you can specify the users and/or groups that will be able to authenticate with SAML.

Step 8 - Authorize an API
The following steps are necessary to support the adoption of accounts in S-Filer Portal
Select API permissions from the left-hand menu, then click on Add a permission.

In the case of S-Filer Portal, you must select Microsoft Graph.

In the next screen, click on Application permissions.

Select the following items:
- Application.Read.All
- Group.Read.All
- GroupMember.Read.All
- User.Read.All
Click on Add permissions

Once the API has been added, you must click on Grant admin consent for [Tenant id].

Finally, click on Yes to confirm administrator consent.

Step 9 - Creating a secret
The last step is to create a secret. To do this, click on Certificates & secrets on the left-hand menu. Go to the Client secrets tab and click on New client secret.

In the box that opens, enter the Description and Expires and click on Add.

Copy the secret value. It will be needed later in step 2 of the S-Filer Portal configuration in the Adoption source tab.

The configuration steps to be performed in the Azure portal are now complete. The next steps take place in the S-Filer Portal administrative console.
Configuration in S-Filer Portal
The following steps take place in the S-Filer Portal administrative console.
Step 1 - Activate the Multidomain feature for the Web client(s)
Log into the Administrative Console using your login details. Open the section identified by the name of your user interface. Open the Configuration section and click on Features. Then activate the Enable "Multi domain" feature for the Web client(s) for which you want to offer Azure SAML authentication.

Step 2 - Create and set up the authentication method
Use the link represented by the server name in the left menu to create a new authentication mechanism.

You must select the Azure AD option as Authentication mechanism.

Enable the authentication mechanism and enter the Tenant ID as configured in the SAML Flow section.
Optionally, you need to determine whether to enable Auto Enrollment. This will enable users who do not have a profile in the solution to complete it after successful SAML authentication. It is not necessary to activate automatic enrolment when adoption is in place, as users will already be present in the database.
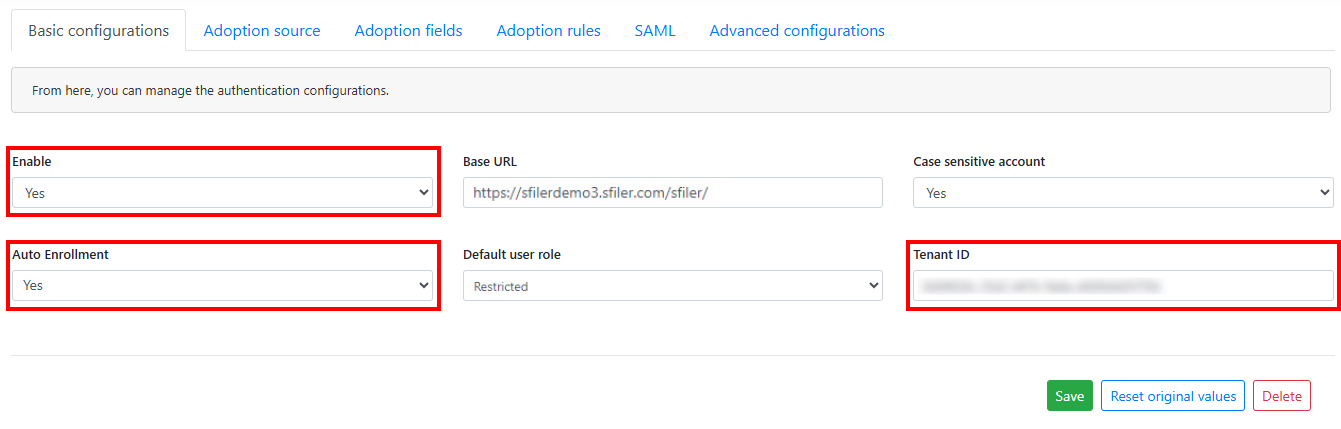
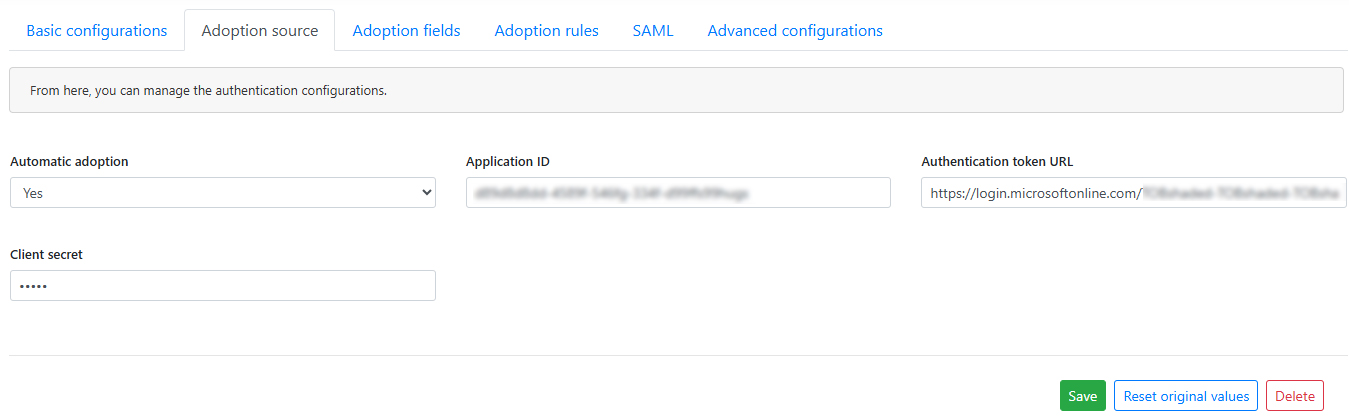
Activate Automatic adoption.
- Enter the URL value of the authentication token configured as follows: https://login.microsoftonline.com/[tenantid]/oauth2/token and replace the [tenantid] with your Tenant identifier.
- Enter the Application ID as configured in the SAML flow section, step 7. This corresponds to the value labeled Application (client) ID in the configuration.
- Enter the Client secret as configured in the SAML flow section.
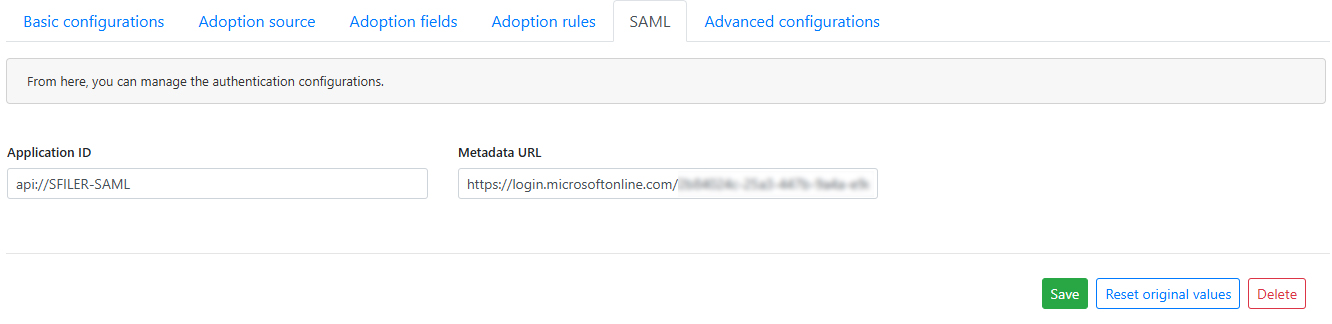
Step 3 - SAML configuration
Finally, you need to enter the Application ID and Metadata URL parameter as configured in the SAML flow section.
See also
Refer to the authentication mechanism configuration documentation for Microsoft Azure for a complete description of all the configuration fields for this authentication mechanism.
Step 4 - Restart S-Filer Portal
To make the changes effective, it is necessary to restart the S-Filer Portal server and Web client. After restarting both components, a new button will become available on the authentication page.

