Integration Guide
S-Filer Portal is a web-based solution for high-security document management and file-transfer. Users can use their web browser to login and securely send confidential files to colleagues throughout the enterprise and around the world.
What is S-Filer Portal
S-Filer Portal is a complete, robust, Enterprise File Synchronization and Sharing (EFSS) and Managed File Transfer (MFT) solution designed to facilitate and secure all your information movement requirements including automated system to system file transfers, community based collaboration and person to person document sharing through synchronized folders.
S-Filer Portal is a dynamic, interactive solution that can be tailored to meet your specific file transfer and sharing requirements. Documents can be easily exchanged through a browser-based interface, a multi-platform command-line interface, a Windows application, synchronised folders under your "My Documents" as well as from mobile devices using secure standard protocols such as FTPS, SFTP, HTTPS.
S-Filer Portal combines ease of use for end users with corporate policy enforcement. "Communities" offer corporate teams and partners a robust, controlled managed file transfer and file sharing environment while "Shares" are designed for professionals who dynamically create self-administered collaboration and sharing spaces with their clients or partners. A lightweight, "ad hoc" mode allows for easy and fast infrequent transfers.
S-Filer Portal takes advantage of multiple sources such as Active Directory (AD), LDAP directories and databases for authenticating and managing corporate and external users. When AD is used for authentication, single sign-on can be provided to corporate users.
Beyond simple file synchronization and sharing, S-Filer Portal includes powerful extensions and API's providing full business process integration such as event driven processing, automation and anti-virus scanning.
S-Filer Portal is an enterprise grade solution built on a strong security backbone offering a comfortable, familiar end user experience. Documents and files are fully encrypted in motion and at rest in all collaboration modes.
This Manual
Who this guide is for
This guide is intended for S-Filer Portal administrators.
The purpose of this manual is to guide you through integration procedures and customisation once the S-Filer Portal Components are installed. You may not need or wish to add or customise any of these features. The Installation has setup all S-Filer Portal components in a usable typical working configuration. This manual covers advanced installation configurations.
Adding a new authentication method
Although S-Filer Portal includes its own authentication database, an organisation would normally prefer to have the solution authenticate users from the corporate authentication server such as an LDAP Directory, Kerberos/Active directory or Custom Authentication.
This section explains how to connect the S-Filer Portal authentication process to the corporate Authentication server and how to adopt all or specific users.
- Connecting to the Administration Console
- Configuring a new Microsoft Active Directory authentication mechanism
- Configuring a new Microsoft Azure authentication mechanism
- Configuring a new OpenID Connect authentication mechanism
- Configuring the adoption scheduler
Connecting to the Administration Console
To add a new authentication method, you need to login to the S-Filer Portal Administration Console.
Launch a browser session.
In the URL field, enter the URL address of your S-Filer Portal's server followed by the port 8090.
For example: https://www.okiok.com:8090
Normally, you would not allow access to this port from the outside, so we assume here that you are accessing from inside the perimeter or that you are connected in VPN.

Enter the username and password of the database used by the S-Filer Portal server.
Once logged-in, in the left hand tree view, click on the server instance you created. In this example, it is called "mycompany_server".

In the server configuration panel you need to choose "Add a new authentication mechanism".
The following dialog box will open.

Choose the authentication name that is meaningful because it will represent the domain name used for all S-Filer Portal accesses with the browser and with the CLI and other protocols.
The Authentication Mechanism can be LDAP Directory, Active Directory Azure AD or OpenID Connect.
For this example, select "Active Directory" and click on the "Add Authentication Mechanism" button to add the Authentication Mechanism.
In the following example the "Okiok" authentication domain was added successfully.
Configuring a new Microsoft Active Directory authentication mechanism
We now need to do the Basic configuration of this new authentication mechanism. It will need to connect to your existing Microsoft Active Directory server in order to adopt and authenticate users.

- Enable: The first thing is set enable to Yes
- Base URL: The base URL is the URL used to access S-Filer Portal and which will be embedded in e-mail notifications, in the example above: https://www.sfiler.com/sfiler/
- Auto enrollment: Permits users in the domain that have not been adopted to enroll. We leave this to no for this example.
- Case sensitive account: This setting indicates whether the authentication provider is case sensitive or not regarding user names. In the example set to No, since Azure AD is not case sensitive for account names.
- KDC address: The KDC address is the IP address or hostname of the Active Directory KDC (Kerberos Key Distribution Center)
- Realm : The Kerberos domain Name, this name must be in uppercase
Configuring the adoption source

- Automatic adoption: Determines whether automatic adoption is active.
- Hostname / IP address: The hostname of the active directory in this example: 192.168.0.4
- Port: The port number to access the active directory in this example: default 389
- Use SSL: Whether to use SSL to contact the Active Directory LDAP port. When using SSL, the default port is 636.
- Follow referral: Set the Follow referral if we must follow LDAP referral (Users in a separate trusted AD domain are sometimes returned as referrals). Note that following referrals can sometimes cause problems if the referrals are not configured properly in the AD domain and the addresses are not reachable. In this example, we set it to Yes.
- Admin user: The Admin account user name to access the active directory.
- Root name: The base DN to use to start the LDAP search for adopting users
- Admin password: The Admin account and password to access the active directory.
- Provider: Name of the Java Class used to connect to the LDAP source.
- Connexion pool size: Number of connections opened. This should be tuned for performance. Normal values are between 1 and 5.
- Idle timeout: timeout before a connexion is dropped.
Selecting adoption fields
In most cases the Adoption fields defined by default do not need to be modified.
For users to be adopted, S-Filer Portal requires a Display name attribute, an Account attribute, an Email attribute and an Identifier attribute.
If some of these fields are missing the user will not be adopted and the server log will have the reason why the user was not adopted.

Setting rules for adoption
The Adoption rules tab is used to manage adoption rules.

Include group member: This option indicates whether the members of a group matching the rule will be adopted or not.
Search depth: Set the search depth for the tree structure in the LDAP search
Default adoption group: If specified, all adopted users will be marked as members of the specified group in addition to the other groups from the LDAP directory. This is useful to have a group including all adopted users.
Create Group: This option indicates whether matching groups in the LDAP search should be created in S-Filer Portal or not.
Email notification: You can set whether the adopted users will have email notification turned on or off by default.
Inclusion filter: This is an LDAP filter expression, this will filter the LDAP elements returned in the search. See this Wikipedia entry for example of LDAP search filters:
http://en.wikipedia.org/wiki/Lightweight_Directory_Access_Protocol#Search_and_Compare
Ex: if you write CN=sfiler in the inclusion filter, S-Filer Portal will only adopt users from the LDAP group sfiler.
Exclusion filter: This is simply a shortcut for adding an LDAP search filter of the form (!(exclusion_filter)). Ex: if you write CN=sfiler in the exclusion filter, S-Filer Portal will adopt all entries except those matching CN=sfiler.
Group list to add: This parameter makes it possible to limit the group creation to certain entries only. This option will be used only if Create Group is set to Yes. Enter a semi-colon-separated list of groups you wish to adopt. If empty, this parameter is ignored and all matching groups will be adopted.
Group list to exclude: This parameter makes it possible to avoid the creation of some specific groups. This option will be used only if Create Group is set to Yes. Enter a semi-colon-separated list of groups you wish to exclude from the adoption.
Advanced Configuration
The Advanced configurations Tab is used only to change the name of the authentication method once it is already created.

Configuring a new Microsoft Azure authentication mechanism
We can also configure the authentication to proceed with Microsoft Azure. It will need to connect to your existing Microsoft Azure service in order to adopt and authenticate users.
Important
You need to have an existing Microsoft Azure service registration in order to be able to proceed with the following configuration.

- Enable: The first thing is set enable to Yes
- Base URL: The base URL is the URL used to access S-Filer Portal and which will be embedded in e-mail notifications, in the example above: https://www.sfiler.com/sfiler/
- Case sensitive account: This setting indicates whether the authentication provider is case sensitive or not regarding user names. In the example set to No, since Active directory is not case sensitive for account names.
- Auto enrollment: Permits users in the domain that have not been adopted to enroll. We leave this to no for this example.
- Default user role: Provides a default role to users adopted from your Microsoft Azure tenant. The possibilities are: Standard, Administrator, Guest and Restricted.
- Force multi-factor authentication (MFA): Determines if multi-factor authentication is required when authenticating users.
- Tenant ID: The unique ID of your tenant.
- Application ID : The ID of your application as defined in the Microsoft Azure configuration API exposure.
Configuring the adoption source

- Automatic adoption: Determines whether automatic adoption is active. If this value is positive, the adoption will be done for this mechanism. The system will then adopt the users from the external user registry into the S-Filer system. Adoption occurs whenever the adoption task runs. This task can be scheduled in the scheduler section of the server configuration.
- Authentication token URL: This URL is used to retrieve the authentication token that is needed to use the Microsoft Graph REST API.
- Client Secret: This is the client secret used to authenticate when retrieving an authentication token.
See also
Selecting adoption fields
In most cases the Adoption fields defined by default do not need to be modified.
For users to be adopted, S-Filer Portal requires an Account attribute, Display name attribute and Email attribute.
It is crucial for the Account Attribute to precisely correspond to the "Name" value that will be retrieved in the SAML assertion. This alignment is essential since the code relies on it to accurately match users.
If some of these fields are missing the user will not be adopted and the server log will have the reason why the user was not adopted.

Setting rules for adoption
The Adoption rules tab is used to manage adoption rules.

- Default adoption group: Enter the list of S-Filer user groups that should be granted automatically to users once adopted. Enter the user group names exactly as they appear in S-Filer separated by ';'. This is useful to have a group including all adopted users. Note that it is important that user groups already exist before adding them here.
- Create Group: Determines whether groups retrieved from the repository should be created in S-Filer.
- Email notification: You can set whether the adopted users will have email notification turned on or off by default.
SAML

- Metadata URL: This URL is used to retrieve the signing key and the logout URL.
See also
Advanced Configuration
The Advanced configurations tab is used only to change the name of the authentication method once it is already created.

Configuring the adoption scheduler
Next we need to activate the adoption schedule. In the left hand navigation tree, expand the server node, expand Scheduler and click on Adoption.

To schedule adoption periodically, make sure that the Enabled field is set to Yes and set the other 2 parameters to the desired values. Click on Save in the upper right corner.
Optionally, you can also use the Start Now button to start the adoption process for all domains immediately.

You will need to restart the S-Filer Portal server and gateway for the changes to take effect.
The S-Filer-server and S-Filer-gateway service must be restarted using Windows or Linux service and not from the Administrative Console.
Now the login page will contain the new domain we just added.
Configuring a new OpenID Connect authentication mechanism
We can also configure authentication to proceed with OpenID Connect. This protocol is supported by several service providers, such as Microsoft, Google and Salesforce. S-Filer Portal will use one of these service providers to authenticate users.
Important
You must have set up your service provider beforehand in order to proceed with the following configuration.

- Enable: The first thing is set enable to Yes
- Base URL: The base URL is the URL used to access S-Filer Portal and which will be embedded in e-mail notifications, in the example above: https://www.sfiler.com/sfiler/
- Case sensitive account: This setting indicates whether the authentication provider is case sensitive or not regarding user names. In the example set to No, since Active directory is not case sensitive for account names.
- Auto enrollment: Permits users in the domain that have not been adopted to enroll. We leave this to no for this example.
- Default user role: Provides a default role to users adopted from your Microsoft Azure tenant. The possibilities are: Standard, Administrator, Guest and Restricted.
- Force multi-factor authentication (MFA): Determines if multi-factor authentication is required when authenticating users.
OpenID Connect Configuration

- Metadata URL: This URL is used to obtain certain parameters required for the rest of the OpenID Connect authentication process.
- Client identifier: Corresponds to the client identifier used to access the service provider to process the authentication.
- Client secret: Corresponds to the client secret used to access the service provider to process the authentication.
- Identity provider: Select your identity provider from the list, or Other if it is not present. The choice of this parameter determines the name and logo of the login button representing this authentication mechanism on the S-Filer Portal Web interface authentication page.
- Identity provider display name: Allows you to customize the name that will be displayed on the login button if the choice of Identity Provider is Other.
- Identity provider custom logo: Name of the file containing the logo used to customize the login button if the choice of Identity Provider is Other. A default logo will be used if this parameter is not specified or if the specified file is not found on the file system. This file must be placed in the client theme at this precise location on the machine where the S-Filer Portal gateway has been installed: /gateway_installation_path/gateway/webapps/sfiler-gui-ajax/themes/your_theme/images/authentication/5.
Advanced Configuration
The Advanced configurations tab is used only to change the name of the authentication method once it is already created.

You will need to restart the S-Filer Portal server and gateway for the changes to take effect.
The S-Filer-server and S-Filer-gateway service must be restarted using Windows or Linux service and not from the Administrative Console.
Now the login page will contain the new domain we just added.
Setting up SSO
S-Filer Portal supports Single Sign on for users authenticated through Active Directory.
This section tries to explain the basic concepts of delegated authentication through the Kerberos authentication mechanism. This will help understand what needs to be configured in both Active Directory and S-Filer Portal in order to get SSO working.
Authentication using Kerberos
In the Windows World the authentication protocol used is Kerberos. The definition given on Microsoft website is the following:
Kerberos is a network authentication protocol that verifies both the identity of the user that is requesting authentication as well as the server providing the requested authentication. The Kerberos authentication mechanism issues tickets for accessing network services. Kerberos clients are applications acting on behalf of users who need access to a resource.
Many detailed explanations of Kerberos and its messages exchange exists on the Web, you can refer to those to get a more thorough understanding. In the following we will explain the few steps to create the service account needed in AD, the KeyTab file that will be stored in both the KDC Kerberos Distribution Center and the S-Filer Portal Server.
Important: Be sure to be very consistent in naming all components including respecting upper case and lower case. The example below shows all screen shots taken on the Okiok.com domain. You should refer to your own domain.
Note: For this authentication mechanism to be successful, one must ensure that there is no more than 5 minutes difference between the Active Directory server time and the S-Filer Portal server time.
Configuring SSO
This following sections explain how to set up S-Filer Portal for SSO.
- Creating an S-Filer Portal service account in AD
- Creating the Kerberos Principal and KeyTab file
- Configuring SSO parameters in S-Filer Portal
Creating an S-Filer Portal service account in AD.
In order to be able to setup SSO, you will need to have access to the Active directory which is the domain controller on which the S-Filer Portal application will run.
In "Active Directory Users and Computers" management panel, click on create new user. The following dialog box will open:

Fill in the required fields.
The second part of the logon name should be your domain.
Click Next, this will bring you to a dialog box to pick a new password as follows:

Enter the password you wish to use and check only "user cannot change password" and "Password never expires". All other check boxes should be unchecked
Once you are done, Click Next and then Click on Finish. The user will be created in the list of users.
Open this new service account to finish editing properties.
 {
{
From the Account tab, validate that the password options are checked, then select from that same scroll list, the encryption type as being AES 256 bit.
 {
{
Creating the Kerberos Principal and KeyTab file
To create a KeyTab file you need to have access to the ktpass.exe application which comes with the Windows Server support tools
Here is an example of how to execute the command considering that the machine which will run S-Filer Portal is on the host www.okiok.com and that the user created in the Active directory is called sfilersso as just created.

ktpass -princ HTTP/www.okiok.com@OKIOK.COM -pass \* -mapuser <sfilersso@>OKIOK.COM -ptype KRB5_NT_PRINCIPAL -crypto AES256-sha1 -out okiok.com-all.keytabor
ktpass -princ HTTP/www.okiok.com@OKIOK.COM -pass \* -mapuser <sfilersso@OKIOK.COM> -ptype KRB5_NT_PRINCIPAL -crypto all -out okiok.com-all.keytabIn the above line, the meaning of the parameters are:
-princ: Specifies the principal name in the form HTTP/www.okiok.com@OKIOK.COM where www.okiok.com is the fully qualified domain name (FQDN) on which S-Filer Portal will run and OKIOK.COM (must be in upper case) is the domain name on which the user account (sfilersso) was created. You should use your own domain name user account. Be very consistent with upper and lower cases.
-mapuser: Maps the name of the Kerberos principal, which is specified by the -princ parameter, to the specified domain account. In this case sfilersso@OKIOK.COM which is the service account name we just created.
-ptype: Specifies the principal type. KRB5_NT_PRINCIPAL is the general principal type and what is recommended.
--crypto: Specifies the key that is generated in the keytab file: must matches the one for user sfilersso or you can choose --crypto all to be more flexible. Selecting DES is not recommended for it is no longer supported in new Windows platform.
-out: Specifies the name of the Kerberos version 5 .keytab file to generate. Once generated, the okiok.com-all.keytab is the file you will copy to the <Server install path >conf folder of the S-Filer Portal Server.
Execute the ktpass command from an administrative dos console:

Once the command completed, save a copy of the KeyTab file in the Server installation Path.
Once this action is done, go back Active Directory Users and Computers" management panel as shown below.
Click on the Account tab

Notice that the user name has changed and is now the principal.
Validate that the password check boxes have not changed and that the encryption algorithm is still the same as selected before.
Configuring SSO parameters in S-Filer Portal
Once you are done with the configuration, start internet explorer and access the URL: https://[CONFIGURED_HOST]:8090/
[CONFIGURED_HOST] should be replace by the exact same configuration used in the configurator's authentication panel in field Keytab principal.
For example: https://www.okiok.com:8090

Select the Basic configuration TAB.
Select and set the following fields:
Keytab file: conf/okiok.com-all.keytab (absolute path or path relative to where your S-Filer Portal server was started)
Keytab principal : HTTP/www.okiok.com@OKIOK.COM
NOTE: Replace OKIOK.COM by your AD's realm, it must be in uppercase. "www.okiok.com" must be the name of the machine where SFiler Portal is installed and it must be recognized by your Domain Controller.
Email configuration
In many contexts, S-Filer Portal sends emails to users and administrators to notify them of various events that occur, such as file transfers, user creation and deletion of communities or files.
This section explains how to configure S-Filer Portal to send emails.
- Connecting to the Administration Console
- Basic email configuration
- Email server configuration
- Basic authentication configuration
- Authentication configuration with OAuth2
Connecting to the Administration Console
To configure emails, you need to login to the S-Filer Portal Administration Console.
Launch a browser session.
In the URL field, enter the URL address of your S-Filer Portal's server followed by the port 8090.
For example: https://www.okiok.com:8090
Normally, access to this port from the public internet is restricted, therefore we assume here that you are accessing from within the internal network or that you are connected in VPN.

Enter the username and password of the database used by the S-Filer Portal server.
Once logged-in, in the left hand tree view, click on the server instance you created. In this example, it is called "mycompany_server". In the same way, then open the drop-down menu under "Configuration". This will allow you to access the "Email" menu.
Basic email configuration
We now need to proceed with the basic email configuration.

- From Name: Sender's name as it will appear in emails sent by S-Filer Portal.
- From Address: Sender's email address as it will appear in emails sent by S-Filer Portal.
- System Error Alert Address: Email address of the recipient who will receive alert emails from S-Filer Portal when a system error occurs.
- System Error Alert Language: Language of alert emails sent by S-Filer Portal when a system error occurs.
- Default notification theme: A theme can be used to customize the content of emails sent by S-Filer Portal. This parameter specifies the default theme that will be used to notify a user who has no specific theme assigned to him.
- Retry period in minutes: Represents the period, in minutes, during which S-Filer Portal will attempt to resend an email that could not be sent. After this time, the e-mail will be destroyed without having been sent. The frequency of retries is configured in the "Email Sender" schedule.
- Notification Path: Path on the file system containing the templates used to create notification emails.
- Subject Extension Filename: Filename suffix of the templates used to create email subject lines.
- Body Extension Suffix: Filename suffix of the templates used to create email subject bodies.
Email server configuration
We now need to configure the email server.

- Email Protocol: Protocol used to send emails.
- Use SSL: Indicates whether the connection to the email server should be secured.
- Use STARTTLS: Indicates whether the server requires the use of STARTTLS, which is an extension of the TLS protocol that involves first establishing an insecure connection with the server before negotiating a secure connection.
- IP address / Hostname: IP address or name of the email server.
- Port: Port used to connect to the email server. Typically, an unsecured connection uses port 25, a secured (SSL) connection uses port 465 and a STARTTLS connection uses port 587.
- Timeout: Represents the number of milliseconds after which the S-Filer Portal server will stop waiting for the email server if the latter has not replied.
Basic authentication configuration
Some email servers can be configured with basic authentication, i.e. you need to provide a user name and password to connect.
This tab lets you configure S-Filer Portal to use basic authentication with the email server.

- Enable: Specifies whether to use basic authentication to connect to the email server.
- User name: User name used to connect to the email server.
- Password: Password used to connect to the email server.
Warning
You must not activate more than one authentication method for the email server (for example, basic authentication and OAuth2). If this is the case, an error will occur when the S-Filer Portal server is started.
Authentication configuration with OAuth2
Some email servers can be configured to connect using the OAuth2 protocol. This tab lets you configure S-Filer Portal to use OAuth2 authentication with the email server.

- Enable: Specifies whether to use OAuth2 authentication to connect to the email server.
- Authentication token URL: URL used to retrieve the OAuth2 authentication token used to access the email server.
- Client identifier: Client identifier used to retrieve the authentication token. Corresponds to the client_id parameter of the OAuth2 protocol.
- Client secret: Client secret used to retrieve authentication token. Corresponds to the client_secret parameter in the OAuth2 protocol.
- Scopes: One or more scope values indicating the resources to which access is to be granted. Corresponds to the scopes concept of the OAuth2 protocol.
- User name: User name used to connect to the email server.
Warning
You must not activate more than one authentication method for the email server (for example, basic authentication and OAuth2). If this is the case, an error will occur when the S-Filer Portal server is started.
S-Filer Portal Web Interface
New security configuration for the S-Filer Portal Web interface.
In the S-Filer Portal Web instance of the S-Filer Portal Administrative console there are new parameters added for security.

Log Level: Set the different log level, the default log level is info. Unless you need to change it for debugging the default level is sufficient.
Default Language: Set the default language for the web interface**.** If users have languages other than the default then S-Filer Portal will display the logon screen in that language.
Secure cookies: Set to YES to have the S-Filer Portal web interface cookies be secured and used in https only.
Configuration Refresh Interval: Set the number of seconds before the configuration will refresh itself. The default is one hour.
Max number of items per list box: This is the number of items to display in a list box. 50 items is the default.
Display Extension option: The default is no. Set this to yes if you want to see the available extensions in the application when you login as an application admin like sfiler-master.
Default Theme: This is the default theme displayed when users login. Users can be in groups which override the default theme.
S-Filer Portal Title: This is the default title that will be displayed in the browser tab. You can change the default to suit your needs.
S-Filer Portal Tree Title: This is the default title that will be displayed in the tree view when you login. You can change the default to suit your needs.
Bottom logo URL: This will set a bottom button logo to a link to Okiok' s webpage.
Use community's name for community labels in the tree: No is the default and will display the community's description in the tree view. Set it to yes to display the name of the community in the tree view.
Clickjacking protection:
HTTP Strict Transport Security:
HTTP Strict Transport Security Maximum Age:
In the S-Filer Portal Web instance of the S-Filer Portal Administrative console this is where you enable or disable Delegated Authentication.

Enable "Multi Domain feature: The default is no. Change to yes if you are using more than one domain for example an Active Directory or any other LDAP. A dropdown is displayed on the login page with the domain names.
Disable auto-completion on logon fields: If this feature is set to yes the fields in the login page won't use auto completion. This means a user will need to enter their username and password each time they login. Set to no If you want your browser to remember your username and password.
Allow administrators to authenticate: The default is yes. If you want an S-Filer Portal admin to connect from the internet. Change to know if you prefer to have them authenticate internally or by using a VPN connection.
Enable "Quick Send" feature: The default is no. Change to yes if you want to send files using an email address. This is intended to securely send a file to a non S-Filer Portal user using an email containing a link to download a file.
Ask for Acknowledgement: After logging in, the user needs to read an acknowledgement page and needs to accept or reject the contents before using the application.
Enable "HTTPS Transfer" feature: The default is no. This feature permits using HTTPS to transfer files. If not enabled this restricts transfers to using the Java Applet for the transfers.
Many modern browser no longer support the Java Applet so it is highly recommended to set this feature to yes.
Acknowledgment source folder: This is the folder that contains the html text that will be displayed on the acknowledgement page.
Ask for license Agreement: The default is no. Set this to yes to have the user read the license agreement before using the application.
License Agreement source folder: The default folder is S-Filer Portal License. It can be changed and this is the folder that contains the html text that will be displayed on the License page**.**
Enable 'Share file" feature: The default is no. Enabling this feature enables an S-Filer Portal user to create a shared folder and invite users to their shared folder using their email address**.**
Display Maintenance Page: The default is no. Enable this to prevent users from logging in during a maintenance and it also displays a maintenance message.
Enable Delegated Authentication: The default is no. Enable this feature to have a third party software take care of supplying the user and domain information in an http header.
Username Header for Delegated Authentication:
Domain Header for Delegated Authentication:
Error codes
- 500 - File not found
- 501 - File is either corrupted or locked
- 502 - File is expired
- 510 - Community not found
- 511 - Ticket not found
- 513 - Move destination is invalid
- 514 - File or folder to move is invalid
- 515 - The destination name is already present in the folder
- 521 - Simultaneous upload of the same file was detected
- 700 - Invalid System License
- 1000 - Authentication failed
- 1001 - Invalid User Name or Password
- 1002 - Password Expired
- 1003 - User Account is locked
- 1004 - User Account is expired
- 1005 - Cannot use S-Filer from this IP Address
- 1006 - User Account does not exist
- 1007 - Domain does not exist
- 1008 - Access Denied
- 1009 - User Account is temporary locked
- 1010 - User needs to accept license
- 2001 - Handshake for Download Failed
- 2002 - Handshake for Upload Failed
- 3000 - Token is Invalid
- 3001 - Token is expired
- 3002 - Token is not yet valid
- 3003 - Token has an invalid signature
- 3004 - Invalid Remote IP
- 4000 - User not authorized to perform this task
- 5000 - Unknown Persistence
- 5001 - Persistence already exist
- 5002 - Email already exist
- 5003 - Email not used by any user
- 5004 - Email used by many users
- 5005 - Email doesn't match user
- 5006 - Connection Lost
- 5010 - Invalid name format
- 5011 - Invalid domain
- 5012 - Invalid length
- 5013 - Invalid email format
- 5014 - Invalid Application
- 5015 - Invalid Application Version. You must upgrade the CLI
- 5016 - You cannot delete yourself
- 5017 - No Permission
- 5018 - Invalid input field value
- 5050 - Extension Not Available
- 6000 - The Password is invalid
- 6001 - The password format is invalid
- 8000 - Unknown Configuration
- 9000 - The Communication failed
- 10000 - Unknown error
- 11000 - Not authorized to delete a file locked.
- 11001 - Not authorized to be administrator. Check your access rights.
- 20000 - Transfer - unknown error
- 20001 - Invalid format for expiration date
- 20003 - The expiration date exceeds the system absolute file retention period
- 30001 - The storage size limit has been reached.
- 30002 - The community storage size limit has been reached.
- 30003 - The user storage size limit has been reached.
- 30004 - The file size exceeds the maximum storage allowed.
Setting up extensions
Extensions enhance S-Filer Portal capabilities beyond simple file transfers by enabling event driven custom processing.
This section covers all aspects of integrating extensions including examples of existing extensions supplied in the S-Filer Portal installation package.
- Activating extensions
- Existing extensions
- Configuring Extension scope
- Command line extension
- Groovy extension
- Transfer Logging Extension
- ICAP filter extension
- MIME based Content Type Filter extension
Activating extensions
In order to use some of the existing extensions, you must first enable using extensions.
Launch a browser with the URL of your server's installation, using port 8090 to access the S-Filer Portal Administrative Console. Ex.:
Enter the username and password for the S-Filer Portal database account.
If you do not remember these, refer to the CheckList at the end of the Installation manual.

In the left hand tree view, expand /SFiler Portal/mycompany_server/mycompany_gui and click on Configuration. In the top navigation tabs, click on Advanced Configuration.
Next you need to change the Display Extension option from no to yes and click save in the upper right corner.

After saving the information, you need to restart the S-Filer Portal server and gateway service.
The S-Filer Portal server and gateway service must be restarted using Windows or Linux service and not from the Administrative Console
Once the application is available you need to login to S-Filer Portal's main application as an S-Filer Portal Administrator. Ex.: https://www.sfiler.com/sfiler/ . The default administrator is sfiler-master and, if you never connected yet, the initial password is sfiler.
Existing extensions
The custom extensions package is automatically installed with S-Filer Portal. This package contains the following extensions:
Command line extension
This extension launches and executes a native command line script. Windows and UNIX based operating systems are supported
Groovy extension
This extension starts an embedded Groovy Shell and evaluates a Groovy script.
For more Groovy information http://groovy.codehaus.org/
ICAP filter extension
This extension decrypts the content of a file and sends it to an ICAP capable device to determine if the content is safe.
MIME based Content Type Filter extension
This extension decrypts the content of a file, determines the content type and then verifies that this content type is allowed.
Transfer Logging extension
This extension log transfers made for specific events.
Batch import extension
This extension simplifies the process of creating users, groups and communities. Simply create a CSV file with user, group and community information and import it into a dedicated community.
Image to PDF extension
This extension transforms an image into a PDF document.
Configuring Extension scope
In the left hand navigation tree, click on Extensions to get a list of current extensions available.

As an S-Filer Portal Administrator you can:
- Add an extension
- Modify an extension parameter
- Remove an extension
The four letters (A G C U) on the right refer to the extension's execution scope.
- A = Application
- G = User Group
- C = Community
- U = User
In the screen shown above, we see that the extension called "ICAP Filter" can be used for the entire application.
As for the order of execution, the events assigned at the application level will be executed first, followed by events assigned to the user groups, those assigned to communities. Events specific to a user will be executed last.
Add an extension
In the left hand navigation tree, click on Extensions. In the right hand panel, click on Add extension.

When you select an extension in the list, we can see its name, description and the implementing java class.
- Execution scope: Select all the desired object on which this extension will be available for assignment.
Click on Add Extension to save the selection
Modify extension scope
In the Left hand navigation tree, click on Extensions. In the right hand panel, click on an extension you previously selected.

- Execution scope: You can change all the desired object on which this extension will be available for assignment.
Note
If you remove an extension from one object, all references to this extension will be removed from the object.
Remove an extension
In the Left hand navigation tree, click on Extensions.
To remove an extension, in the right hand panel, simply select the checkbox associated to the extension you with to delete and press Delete.

Extension Usage
The previous section showed how to configure the execution scope of an extension. This section explains how to use these extensions in each of these objects instances (Users, Groups and Community, as well as globally for the entire Application).
In all 3 panels displaying the list of users, groups and communities, a button to assign extension to each of these elements is present:  This button allows you to manage the extensions assigned to the objects from that particular list. You will therefore understand that you can assign an extension to a group of users, a community and even to a specific user. When you click this button, a window similar to this one will be presented:
This button allows you to manage the extensions assigned to the objects from that particular list. You will therefore understand that you can assign an extension to a group of users, a community and even to a specific user. When you click this button, a window similar to this one will be presented:

From this screen, one can see that 2 extensions are available at the Application level and both are active.
The following actions are available:
- Assign an extension
- Modify an extension
- Apply a Filter on the list
- Remove an extension from this object
An extension can be configured globally under Extensions / Application Extensions in the left tree view or it may be assigned to:
- A user
- A user group
- A community
To access this configuration panel, look for the  icon at the far right of the user, user group or community or in the left tree view. See example below for user groups.
icon at the far right of the user, user group or community or in the left tree view. See example below for user groups.

Extension configuration panel

- Name: Provides a specific instance name for this extension configuration.
- Available Extension: Lists all extensions available.
- Active: Active or Not.
- Processing order: The order in which the extension will be executed in relation to other configured extensions.
- Extended configuration: Some extensions have specific configuration, when you select an extension that has these specific configuration, they will appear in this section.
- Execution Events: Events for which the extension will be invoked.
Once you are happy with your selection, click on Assign this extension.
The initialization parameters are loaded when the extension is created. Those parameters can be updated through the User Interface. The configuration will be read from the database before each execution.
The following sections demonstrate the usage of the supplied Extensions.
Modify extension assignment
From any of the 3 lists (users, groups or communities), select a line where an entity is present and click on the extension button at the far right of the line of your choice.
Apply a filter on the list
Applying a filter is very useful to determine which extension will be invoked on a specific event. From the extensions assignment panel, one can also see in what order these extension will be invoked.

Remove an extension assignment
To remove an extension assignment from an object, simply select the checkbox associated to that extension assignment and press Delete.
Command line extension
This extension launches and executes a native command line script. Windows and UNIX based operating systems are supported
Configuration
The initialization parameters are loaded from the configuration file when the extension is created. Those parameters can be updated through the User Interface. The configuration will be read from the database before each execution.
These are the configuration properties available specifically for the extended configuration section. Of the panel when you select the Available Extension called Execute Native Command

Command to execute: Native command to be executed. Shall be contained in a file and this configuration is the absolute path to reach this script.
Working directory: The decrypted file will be written at this location.
Signature: This field is evaluated when the extension is created or modified, it contains the MD5 file signature. This field is evaluated before each execution. If the file to be executed has been altered the command won't be executed. The signature field should be updated manually. In order to refresh it, go in the configuration panel and update it.
Command parameters: i.e: {DOCUMENT NAME}. Those named parameters will be replaced and evaluated at runtime. The available parameters can be found in the table below.
Important: Those fields must be separated by a space. (i.e : {DOCUMENT NAME} {DOCUMENT SIZE})
| Command Parameter | Description |
|---|---|
| DOCUMENT_NAME | Document Name |
| DOCUMENT_SIZE | Document size in bytes |
| DOCUMENT_IS_FOLDER | True if uploaded document is a folder |
| CONNECTED_USER_NAME | Connected user name |
| DOCUMENT_UUID | Document Unique Identifier |
| SENDER_NAME | Document Sender Name |
| RECIPIENT_COMM_IDS | Community ID |
| RECIPIENT_COMM_NAMES | Community Name |
| PATH | File Path (in S-Filer Portal) |
| TRANSFER_PROTOCOL | Protocol |
Example script and its configuration
The following example will output the configuration properties available to the script and provided by S-Filer Portal at execution time.
Copy the following code in a text file called script.bat.
echo Output of configure properties = document name: %1, document size:
%2, document is a folder: %3, connected user name: %4, document UUID:
%5, sender name: %6, community ID: %7, community name: %8, path: %9,
transfer protocol: %10 \> \"c:\\temp\\output.txt\"This line will output the properties that S-Filer Portal can give to the executing script. The arguments %1 to %10 refers to the fields and order defined in Command parameters field in the next step.
S-Filer Portal configuration
From the S-Filer Portal main screen, select <Communities>. Click the  icon at the far right of one community.
icon at the far right of one community.
In the next panel, click on <Assign extension>.
In the Extension Assignment panel that opens, enter a Name, Select Execute Native Command for Available extension, select Yes for Active, and enter 100 for Processing order.
Next we will fill the Extended configuration. In the Command to execute, enter the full path to your script you created in the previous sub section. Enter a Destination folder. You may take the same location where your script is located. Leave the Signature field empty, it will be filled automatically when you click on Save. On the Command parameters, enter the following line (see Output Parameters):
- DOCUMENT_NAME
- DOCUMENT_SIZE
- DOCUMENT_IS_FOLDER
- CONNECTED_USER_NAME
- DOCUMENT_UUID
- SENDER_NAME
- RECIPIENT_COMM_IDS
- RECIPIENT_COMM_NAMES
- PATH
- TRANSFER_PROTOCOL
On the right hand part of the panel, select "On Upload Completed"

Click on Assign this extension.
Log out and connect with a user that is part of this community and transfer a file to this community. At the end of the file transfer, go in the previously configured folder and locate the file output.txt. It should contain the configured properties in the extensions. Ex.:
Output of configure properties = document name:
Extension-modification.jpg, document size: 156825, document is a folder:
false, connected user name: a1, document UUID:
7f15af19-92fc-43a2-963e-001389eae935, sender name: a1, community ID: 9,
community name: CommA, path: applet, transfer protocol:
Extension-modification.jpg0Groovy extension
This extension gives the ability to execute a Groovy script. These extensions start an embedded Groovy Shell and evaluates a Groovy script.
The Groovy Shell allows S-Filer Portal to pass in and out variables via the Binding object.
For more Groovy information http://groovy.codehaus.org/
Configuration
The initialization parameters are loaded when the extension is created. Those parameters can be updated through the User Interface. The configuration will be read from the database before each execution.

Script to execute: Script to be executed. Shall be contained in a file and this configuration is the absolute path to reach this script.
Signature: This field is evaluated when the extension is created or modified, it contains the MD5 file signature. This field is evaluated before each execution. If the file to be executed has been altered the command won't be executed. The signature field should be updated manually. In order to refresh it, go in the configuration panel and update it.
Destination Folder: Destination Folder. The decrypted file will be written at this location.
| Command Parameter | Description |
|---|---|
| DOCUMENT_NAME | Document Name |
| DOCUMENT_SIZE | Document size in bytes |
| DOCUMENT_IS_FOLDER | True if uploaded document is a folder |
| CONNECTED_USER_NAME | Connected user name |
| DOCUMENT_UUID | Document Unique Identifier |
| SENDER_NAME | Document Sender Name |
| IS_UPLOAD | True if this was an upload |
| IS_COMPRESSED | True if the document is compressed |
| INPUTSTREAM | Input stream, the decrypted document is available through this stream |
Sample Groovy Script
The sample script writes the uploaded file to a local file.
// The uploaded document is written to dest_folder/document_name
new File(dest_folder+"/"+document_name).append(inputstream)
// Return 0 for a valid execution, any other value if the execution must stop
return 0The variables dest_folder, document_name and inputstream are injected by S-Filer Portal into the script.
The script return 0 to the extension. The script must return a value. If a value different from 0 is returned S-Filer Portal will consider the script execution in error and will stop the extension chain execution.
Groovy Basics
The intent of the following section is to provide some basic groovy knowledge (most of this examples can be found in the Groovy documentation). This is not a Groovy programming tutorial. For the complete Groovy documentation please follow this link http://groovy.codehaus.org/
In general
- The semicolons are optional
- The following packages and classes are imported by default
- java.io.*
- java.lang.*
- java.math.BigDecimal
- java.math.BigInteger
- java.net.*
- java.util.*
- groovy.lang.*
- groovy.util.*
- The return statement is not required by Groovy but is required by S-Filer Portal to control the extension execution flow.
Output a string or variable to the standard output
println **\"Hello!\"**
//Output dest_folder variable(injected by S-Filer Portal)
println dest_folderConditional execution
amPM = Calendar.getInstance().get(Calendar.AM_PM)
if (amPM == Calendar.AM)
{
println("Good morning");
}
else
{
println("Good evening")
}Transfer Logging Extension
This extension log transfers made for specific events.

ICAP filter extension
This extension decrypts the content of a file and sends it to an ICAP capable device to determine if the content is safe.

| Attribute | Description | Example |
|---|---|---|
| Configuration | Description | |
| Hostname | The IP address or the hostname of the ICAP server | Icap.example.com 192.168.0.50 |
| Port | The port on which to connect (default: 1344) | 1344 |
| URI | The query string to use. Many ICAP servers use the Query string to pass parameters. The exact syntax depends on your ICAP server. | Refer to your ICAP |
| Use REQMOD | Whether to use REQMOD or RESPMOD in ICAP protocol. The default value (false) will use RESPMOD and should work for most ICAP servers. Use REQMOD only if advised from Okiok support. | True (to use |
| SSL Connection (true/false) | Whether the ICAP server listens using an SSL (or TLS) connection | True (to use SSL) False (to use plaintext) |
To use SSL connectivity, you need to import the ICAP server certificate into the management console's certificate manager. On first connection, the certificate will be considered as an "unknown certificate". An operator must therefore accept it before it is considered valid. Once validated, the communication between S-Filer Portal and the ICAP server is possible.
MIME based Content Type Filter extension
This extension validates whether a file extension is allowed and ensures that it is. If the file extension is not allowed, the file is deleted.
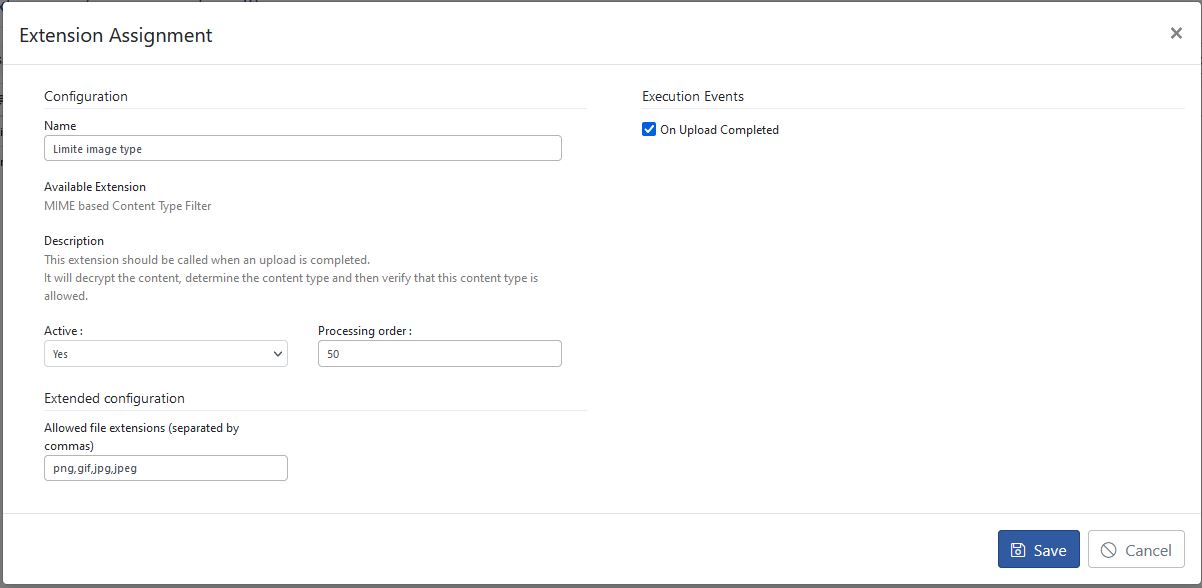
The extension allows you to limit the type of content based on the file extension, but does not go as far as to check the file content. It's a simple way of limiting the types of files that can be transferred via S-Filer Portal, but it won't prevent a malicious user from renaming a file to bypass content type checking. To configure this extension, you need to provide a comma-separated list of allowed file extensions.
Batch Import Extension
This extension requires several steps before it can be used.
- You must create a community that will be used to upload the CSV import file.
- You must then create a user template from which the users to be imported will be created.
- Repeat the previous step and create a group template from which to create the groups to be imported.
- Repeat the previous step and create a community from which to create the imported communities.
- You must assign the extension to a community and ensure its access to restricted users responsible for the import.
- Create a CSV file containing information on the users to be imported.
- Drop the CSV file into the community created in step 1.
To enable import, it is necessary to create a user, group and community template. These entity templates can be created from the web interface in the same way as a normal entity. The only difference is that these entities will not be used directly by the solution. They will be used by the batch import extension to create the actual entities. It is advisable to use a distinctive name to easily distinguish these entities from those actually affected. Once the entities have been created, it is necessary to configure the extension by specifying the names of the previously created entities.

When it's time to import users, simply drop the CSV file into the community created in step 1. If the process works correctly, users, groups and communities will be created. If the process doesn't work as expected, an error file will be created in the directory of the community used to perform the import. This file will contain the error entries that occurred during import. You can download the file and analyze the errors in order to correct the problematic entries and restart the import from the corrected file.
The CSV file format is as follows:
| Field | Description | Example |
|---|---|---|
| User | This field represents both the user and the user's e-mail address. | john.doe@okiok.com |
| Full Name | The user's full name. | John Doe |
| Language | The user's language (permissible values are: fr, en, es, de and it). | fr |
| Group | The name of the user's group (if the group doesn't exist, it will be created using the template passed as a parameter in the extension configuration). | My group |
| Community | The name of the user's community (if the community doesn't exist, it will be created using the template passed as a parameter in the extension's configuration). | My community |
| Default community | A flag (true / false) indicating whether the community passed as an argument should become the user's default community. | true |
Here is an example of a CSV file:
"john.doe@okiok.com","John Doe","en","My group","My community",true
"alice.monroe@okiok.com","Alice Monroe","en","My group","My second community",falseIn this example, we have two users to import. The first user is "John Doe" and the second is "Alice Monroe". At the end of the import process:
- Both users will be created and assigned to the "My group" group.
- User "John Doe" will be assigned to the "My community" community, which will be set as this user's default community.
- The user "Alice Monroe" will be assigned to the community "My second community", which will not be defined as this user's default community.
To add a user to several groups, simply duplicate the line for the same user. For example:
"john.doe@okiok.com","John Doe","en","My group","My community",true
"john.doe@okiok.com","John Doe","en","My group 2",,trueOn completion of the import, the user "John Doe" will be assigned to the "My group" and "My group 2" groups. Note also that the community is not specified for the second line. The user is already a member of the "My community" community via the first "My group" group assigned to the first line. It is therefore not necessary to specify the community for the second line.
The same logic applies to assigning users to multiple communities. For example:
"john.doe@okiok.com","John Doe","en","My group","My community",true
"john.doe@okiok.com","John Doe","fr","My group","My community 2",trueOn completion of the import, the user "John Doe" will be assigned to the communities "My community" and "My community 2". Note also that the group is specified for the second line. This is necessary, as the user must be assigned to a group in order to be assigned to a community.
Import users from an external domain
Importing users from external domains such as LDAP or Azure AD cannot work in the same way as importing local users. This is because external users cannot be created directly in S-Filer Portal, as they are managed by an external system. They must therefore be created before the import process can be launched. A simple way of doing this is to request initial authentication of the external user. This authentication will automatically create the user in S-Filer Portal. The import process can then be used to assign groups and communities to the user.
PDF Conversion Extension
The purpose of this extension is to transform an uploaded image into a PDF document according to the extension's configuration parameters. This extension is very useful when there are expectations as to the final format of documents, and saves recipients from having to manually transform the document they receive.

The extension uses the following configuration parameters:
| Field | Description |
|---|---|
| Horizontal border | The resulting horizontal border of the image in the PDF file. |
| Vertical border | The resulting vertical border of the image in the PDF file. |
| Horizontal floating position | The horizontal floating position of the image in the PDF file. |
| Vertical float position | The vertical float position of the image in the PDF file. |
| Image width | The width of the resulting image in the PDF file. |
| Height of image | The height of the resulting image in the PDF file. |
The originally uploaded image will remain unchanged, and a PDF document will be created from it.
Migrating users from one domain to another domain.
This section presents the steps necessary to migrate users from one domain to another domain. All existing user information (groups, communities and files) are copied to the new user.
I have two different domains in the S-Filer Portal Admin console, the old domain support.com and the new domain sfiler.support.com.
It's important to have the Domain ID number for the utility we are going to use for the migration.
This information can be found in the S-Filer Portal database using the table Domain.
In my case you can see from the Figure 67 that support.com has an ID of 3 and sfiler.support.com has an ID of 4.

Using the Administrative Console:
We will activate the adoption for the domain support.com and to facilitate the migration we will have all the S-Filer Portal users we want to migrate in the S-Filer Portal AD group.

For the sfiler.support.com domain we will activate the authentication but not the adoption.
We do not need to adopte the users in the sfiler.support domain because the modify-user function will adopt the user during the migration.
We will use the Administrative console to activate the authentification for the target domain:

Here we will deactivate the adoption for the target domain:

Here is an example of using sfiler-admin to migrate users from the support.com domain to the sfiler.support.com domain.
We will use the modify-user option of sfiler-admin.
- The --d parameter is the ID of the source domain support.com.
- The --n parameter is the user name.
- The --domain parameter is the ID of the new domain sfiler.support.com.
- modify-user -d 3 -n ad-2-user -domain 4
Below is a PowerShell script you can use for the migration.
sfiler-admin-move-user:
cls
Set-PSDebug -Trace 0
cd C:\temp\sfiler-powershell-scripts
set-item -path Env:CLASSPATH -value C:\temp\sfiler-powershell-scripts
"CLASSPATH = $Env:CLASSPATH"
$Command = "C:\temp\sfiler-powershell-scripts\sfiler-admin.exe"
Write-Host "-------------------------------------------------"
Write-Host -Fore Green "CLASSPATH: $env:CLASSPATH"
Write-Host -Fore green
& $Command -v -l sfiler-master -p password -s https://www.sfiler.com/sfiler/server modify-user -d 3 -n ad-2-user -domain 4
& $Command -v -l sfiler-master -p password -s https://www.sfiler.com/sfiler/server modify-user -d 3 -n ad-3-user -domain 4
& $Command -v -l sfiler-master -p password -s https://www.sfiler.com/sfiler/server modify-user -d 3 -n ad-4-user -domain 4
& $Command -v -l sfiler-master -p password -s https://www.sfiler.com/sfiler/server modify-user -d 3 -n ad-5-user -domain 4
echo $lastexitcodeBelow is an example of the PowerShell script and execution:

Once we migrate a user from the support.com domain we must remove that user from the group. In my example it was the user in the S-Filer Portal AD group.
For the migrated users all information (groups, communities and files) will be same the user had with the old domain name.
Once all users are migrated you need to reactivate the adoption on the target domain.
The Adoption source:

This completes the migration of users from one domain to another domain.
Using the Admin API
This section presents the steps necessary to use the admin cli jar as a base for integration in a java project.
Class path
In order to have access to the administrative command line interface's functions in a development environment, you need to include cli-admin.jar in your project's class path.
Base class
The base class you need to use is com.okiok.sfiler.cli.admin.Main. This class contains a static public method called execute. This is your entry point to pass commands to the api.
When you call execute, if all went well, the method will return an integer 0, and otherwise a 1 will be returned.
Syntax
First you must generate a string variable containing in order:
- All needed common options, refer to :[Common Options]
- Command to be executed,
- Command specific options
In the syntax form shown below
String[] params = <common options>, command,<Command options>;
Main.execute(params);Where options should be in the form
"-l",UserName, "-p",password, "-s",ServerURLExample of an API call
Following is an example of how to setup the parameter string and actual API call, using the delete user command. You can then apply this to all other administration commands.
Delete-user
| Command options | Required/Optional | Description |
|---|---|---|
| -d | The ID of the domain of the user to delete. | |
| -n | The name of the user |
Example:
String[] params = {"-l", "sfiler-master", "-p", "012345", "-s", "https://www.sfiler.com/sfiler/server/", "delete-user", "-n", "myuser"};
Main.execute(params);