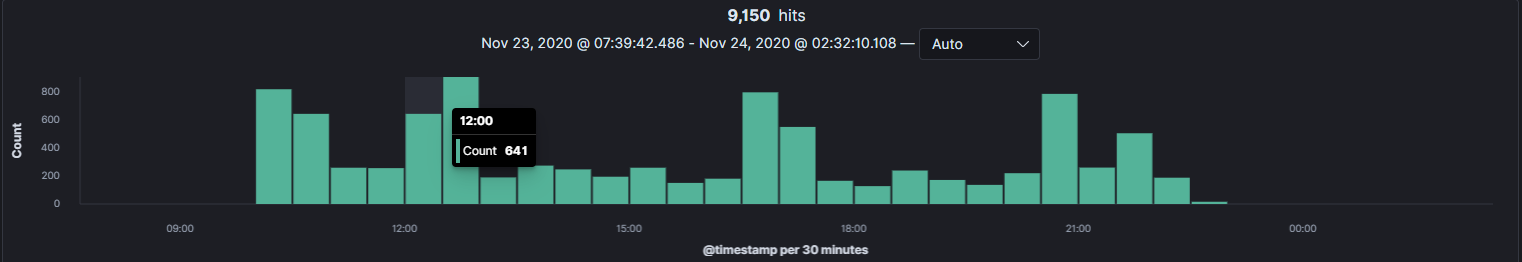
In this post, I’ll explain how to initially setup a SIEM so you can receive your first logs.
This is the second post of the series “SIEM 101″ where I explain the basics of a SIEM, from installation to simple usage. You can see the previous post SIEM 101 — Introduction.
I decided to write the series using Logz.io because they offer an easy to use platform with a free 1GB/day trial with a smooth learning curve. Of course they don’t offer all the features in the free version and some crucial features for a SIEM are missing, but this is perfect to get started with a SIEM! For the Splunk fans, I’ll probably write a blog post about why I don’t recommend it often and why I recommend an Elasticsearch based SIEM most of the time.
First step: open an account
The first thing to do is to open an account on Logz.io. They offer to open an account using your google account, or to register with an email. For this demo I’ll use the google SSO option. So head over to Logz.io and register: https://app.logz.io/#/login
Next, click on “Sign in with Google”:
You’ll get redirected to the Google SSO. Select your existing account, login or create an account. I’ll let you figure this part out.
Then, once back on the Logz.io website, you get a Sign up page. Fill out the details and click “Create Account”:
Note: It is smart to choose a region close to where you live to get better bandwidth when sending logs.
That’s it, your account is ready to receive logs! When you login, you can follow their tutorial if you want to. The next step in this post is pretty much the same thing as their tutorial.
Second step: start sending logs
Now that we have an account, we can finally start sending logs. Make sure you are logged in your account for the next steps. I divided this section in two, one for Windows and one for Linux (I use Ubuntu).
Once logged in, click on “Send Your Data” in the top navigation:
The next steps are starting to get interesting. We’ll configure the log shipper agents on Windows and Ubuntu.
Windows
On the left navigation, close “Log Shippers” that should be opened, and open “Operating Systems”:
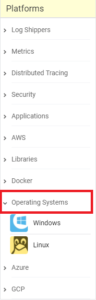
Select “Windows” under the “Operating Systems” menu. Your page will refresh to the URL https://app.logz.io/#/dashboard/data-sources/Windows
They propose 2 options; we are interested in the option 1: Winlogbeat.
As they explain in the page, you first need to install Winlogbeat. So that’s what we’ll do.
Head over to https://www.elastic.co/downloads/beats/winlogbeat-oss and download the right MSI version for your computer (32 bits or 64 bits, if unsure use the 32 bits). For me, that’s the 64 bits MSI:
Note: here, my link is slightly different than the one they propose on their website. This is because I recommend using the OpenSource version (oss).
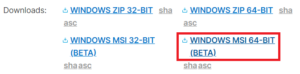
When the download is finished, click the downloaded file, a window will open.
Check the “I accept the terms in the License Agreement” checkbox and click “Install”:
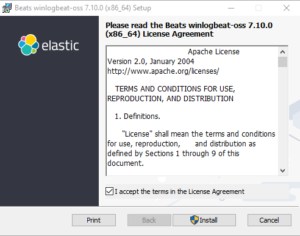
When prompted, accept to run as Administrator (UAC). When the installation is done, click Finish (we leave the checkbox “Open winlogbeat data directory in Windows Explorer” checked.
In the Windows Exporer window that opened at the location “C:\ProgramData\Elastic\Beats\winlogbeat”, rename the file “winlogbeat.example.yml” to “winlogbeat.yml”.
Open your favorite text editor (it can be Notepad, I use VSCode) as Administrator (right click, Run As Administrator) and then open the file “winlogbeat.yml”.
Replace all the content of the file with the content from this gist:
https://gist.github.com/tristandostaler/dcd092192409c7a29cb6489eddbca4b7
In this content, you’ll find the text “YOURTOKEN_PLACEHOLDER”; replace this with the token they provide in the Logz.io settings page in the section “Account settings”:
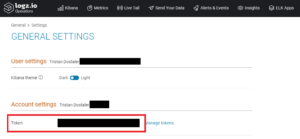
Becareful, this token is secret! If someone get his/her hand on this token, they can send fake data to your account and overload it with garbage data.
Now, download the Logz.io public certificate and place it in “C:\ProgramData\Winlogbeat\COMODORSADomainValidationSecureServerCA.crt“. This certificate is available at https://raw.githubusercontent.com/logzio/public-certificates/master/AAACertificateServices.crt. You’ll need to do this using your text editor as Administrator.
When this is done, run the following command in a PowerShell window as Administrator: Restart-Service winlogbeat
That’s it, you should now receive your Windows logs in Logz.io! Head over to “Kibana” to see them come in (click “Refresh” if you don’t see them right away).
Note: You might have noticed that in the winlogbeat.yml I enabled logging of Sysmon. I plan to make a blog post to explain what is Sysmon and how to use it. For the moment, it doesn’t mather if Sysmon is not installed, Winlogbeat will simply ignore this config line.
Hint: You can enable the Dark Theme for Kibana in the Logz.io settings page
Ubuntu
Note: There is a TL;DR; section at the end. For this section, I assume you know how to use the Command Line Interface (CLI). For Ubuntu, we will be using Filebeat. By default, if you send logs using rsyslog, the data will not be encrypted over the internet, which is not recomended. By using filebeat, we can send encrypted data easily. On the left navigation, in “Log Shippers” that should be opened (if not, open it), click on “Filebeat”. As they explain in the page, you first need to install Filebeat. So that’s what we’ll do. Run the following commands: Note: here, my link is slightly different than the one they propose on their website. This is because I recommend using the OpenSource version (oss).
curl -L -O https://artifacts.elastic.co/downloads/beats/filebeat/filebeat-oss-7.10.0-amd64.deb sudo dpkg -i filebeat-oss-7.10.0-amd64.deb rm filebeat-oss-7.10.0-amd64.deb
We also need the Logz.io public certificate. Run the following command:
sudo curl https://raw.githubusercontent.com/logzio/public-certificates/master/AAACertificateServices.crt --create-dirs -o /etc/pki/tls/certs/COMODORSADomainValidationSecureServerCA.crt
Next, we’ll configure filebeat to ship the logs to Logz.io using my default template and some bash-foo. When asked for the token, provide the token available in the Logz.io settings page in the section “Account settings”:

Becareful, this token is secret! If someone get his/her hand on this token, they can send fake data to your account and overload it with garbage data.
Run the following commands:
sudo curl https://gist.githubusercontent.com/tristandostaler/7a212a0ba23b97c97a5e2c6925bde240/raw/72c90076cf4aa16179c123316b3ef8cec775d576/filebeat.yml --create-dirs -o /etc/filebeat/filebeat.yml echo -n "Please enter your logz.io Token: " && read -s LOGZ_TOKEN && sudo sed -i "s|YOURTOKEN_PLACEHOLDER|$LOGZ_TOKEN|g" /etc/filebeat/filebeat.yml
Now we only need to start FIlebeat and the logs will start shipping! Run the following command:
sudo systemctl start filebeat || sudo service filebeat start (sudo systemctl enable filebeat) || (sudo update-rc.d filebeat defaults && sudo update-rc.d filebeat enable)
That’s it, you should now receive your Ubuntu logs in Logz.io! Head over to “Kibana” to see them come in (click “Refresh” if you don’t see them right away).
Note: You might have noticed that in the filebeat.yml I enabled logging of many systems that are not installed by default, like auditd. I plan to make a blog post to explain what is auditd and how to use it. For the moment, it doesn’t mather if auditd is not installed, filebeat will simply ignore this config line.
Hint: You can enable the Dark Theme for Kibana in the Logz.io settings page
TL;DR; putting all the commands together:
curl -L -O https://artifacts.elastic.co/downloads/beats/filebeat/filebeat-oss-7.10.0-amd64.deb sudo dpkg -i filebeat-oss-7.10.0-amd64.deb rm filebeat-oss-7.10.0-amd64.deb sudo curl https://raw.githubusercontent.com/logzio/public-certificates/master/AAACertificateServices.crt --create-dirs -o /etc/pki/tls/certs/COMODORSADomainValidationSecureServerCA.crt sudo curl https://gist.githubusercontent.com/tristandostaler/7a212a0ba23b97c97a5e2c6925bde240/raw/72c90076cf4aa16179c123316b3ef8cec775d576/filebeat.yml --create-dirs -o /etc/filebeat/filebeat.yml echo -n "Please enter your logz.io Token: " && read -s LOGZ_TOKEN && sudo sed -i "s|YOURTOKEN_PLACEHOLDER|$LOGZ_TOKEN|g" /etc/filebeat/filebeat.yml sudo systemctl start filebeat || sudo service filebeat start (sudo systemctl enable filebeat) || (sudo update-rc.d filebeat defaults && sudo update-rc.d filebeat enable)
Conclusion
That’s it, you now have your initial setup for a SIEM, with logs being sent! Of course, at the moment there are no alerts and the platform we are using don’t offer all the features we would like from a SIEM. But this is perfect to start learning to use a SIEM! In the next blog post SIEM 101 — Basic usage, I explain the basic usage of Logz.io, how to search logs, how to create an alert, etc.
This post was originaly published on https://www.tristandostaler.com/siem-101-initial-setup/ on Nov 24, 2020